The Papers of Seymore Wainscott: The legendary Six-Square Cipher
By Al R. Young
This article presents the transcription of a document, from The Wainscott Collection, entitled Personal Memorandum: A Brief Description Of The Six Square Cipher. As the memorandum itself declares, the original document was created by Seymore Wainscott as a personal reminder of how the cipher works.
The folio in which the memorandum was found also contained two sheets of paper, later identified as some of Seymore's worksheets prepared in creating and refining the cipher. Those worksheets are presented here with scant annotation. One of the sheets presents an early version of what Seymore referred to as pennants, mentioned in Seymore's memorandum. The other sheet contains ideas about enhancing the cipher through further work with the pennants.
Nothing in the folio contained a date. Accordingly, any attempt to assign a date would be speculative. While the history of lytfolc ciphers has yet to be written; indeed, with the task of cataloging The Wainscott Collection still in its infancy, and perusal of the documents and artifacts in the collection just beginning, the present is a time to let the documents speak for themselves. Nevertheless, it appears that cipher and other forms of encrypted communication had had a long history before Seymore was even born.
Seymore's reminiscences appear to remark a thread of interest in the subject from his early youth, for he mentions his childhood fascination with "secret alphabets," and his preoccupation with the very idea of coded messages carried by the couriers that were so prominent a feature of his youth (owing to Bevel Wainscott's sprawling enterprise). Most importantly, however, Seymore speaks at length of his experience with his maternal grandfather, the great Foliaceous Gatherum.
When Bevel and his small household relocated to Lanham in 1757, Seymore, along with the rest of the family, was caught up in the devastating consequences of Bevel's illness. During that time, Foliaceous reached out to his grandson, undoubtedly perceiving much of kindred interest and ability in the youth. In order to throw a lifeline to Seymore during those troubled times, Foliaceous not only reached out to the youth, but did so in terms of Seymore's own interests and imagination. The bond between the two was fixed for life, and set Seymore's feet upon the high road he traveled throughout his life. Grandfather and grandson exchanged encrypted letters even though they were essentially living in the same household. And one of the facets of the exchange was Seymore's exposure to the languages by which the lytfolc had labored for centuries to preserve their history; languages that in times of peril had involved codes and ciphers, tokens and clues of amazing invention.
A Brief Description Of The Six Square Cipher
Created By Seymore Wainscott
The following sequence of 36 characters is referred to hereafter as the stream: ABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890
Draw a grid six cells high and six cells wide.
Starting with the northwest cell, and assigning characters from the foregoing string (one at a time to each cell in the grid) assign the characters moving south until the end of the column, then move to the next (eastern) column and continue assignment until the last character in the stream is assigned to the cell in the southeast corner of the grid. The following columns present the desired arrangement of values in the cells in the grid. This is referred to as the constant grid.
A G M S Y 5
B H N T Z 6
C I O U 1 7
D J P V 2 8
E K Q W 3 9
F L R X 4 0
The constant grid looks like this:
Create a list of 36 words. The following list of names is only an example. Any names or words will suffice; nevertheless, these words will serve as key words; for example, telling a coded-message recipient how the sender's grid is configured. Inasmuch as a keyword may appear in correspondence or in some other means of communication that is more or less public, care should be taken to select key words that can be used in such means of communication without attracting attention. Names of individuals were chosen for this list because they could more readily be used in statements seeming to be of a personal nature. This list is referred to as the key-word list.
Hominy
Mulberry
Rosette
Transom
Newel
Tracery
Finial
Burrow
Signet
Rune
Pargetry
Ovolo
Boss
Anthem
Medallion
Penton
Sorrel
Lupine
Thwaite
Folio
Quarto
Corbel
Scotia
Lilium
Calyx
Currant
Quince
Marjoram
Lichen
Tasselin
Teviot
Sable
Gentian
Trillium
Lancet
Acorn
Draw another grid six cells high and six cells wide.
Assign each name in the key-word list to a cell in the empty grid. The order in which the names are assigned is of no moment. In the following grid, the names were assigned (north-to-south and west-to-east) in the order in which they appear in the key word list. This is referred to as the key-word grid.
Hominy Finial Boss Thwaite Calyx Teviot
Mulberry Burrow Anthem Folio Currant Sable
Rosette Signet Medallion Quarto Quince Gentian
Transom Rune Penton Corbel Marjoram Trillium
Newel Pargetry Sorrel Scotia Lichen Lancet
Tracery Ovolo Lupine Lilium Tasselin Acorn
The key-word grid looks like this:
The cipher is now ready for use in transmitting messages. The remaining steps should be repeated for each instance of the cipher's use.
Draw another grid six cells high and six cells wide.
Select the name of a cell, in the key-word grid, at which to begin assigning stream values. For example, if Lilium is the keyword chosen for this purpose (that is, for creating a particular coded communication), the values in the stream are assigned beginning with the cell named Lilium in the key-word grid. The first four assignments of stream values look like this in the grid just drawn,
Stream values must be assigned in the order in which they appear in the stream. Their assignment begins with the named cell from the key-word grid and progresses from west to east in the manner indicated in the following grid. Note that stream values, in the following grid, wrap back to the grid's northwest cell when the southeast cell is filled, and values continue to wrap around the grid until the stream reaches its beginning at the Lilium cell. This grid is called a message grid, whose key word is Lilium.
D E F G H I
J K L M N O
P Q R S T U
V W X Y Z 1
2 3 4 5 6 7
8 9 0 A B C
Given the stream-value cell assignments in the constant grid, the following list presents the letter equivalents for a coded message whose key word is Lilium.
For example, to write SEYMORE in cipher, according to the foregoing message grid, the person writing the message would first look for the location of S in the constant grid. In the constant grid, S is located in the 4th column and on the 1st row. Now, referring back to the message grid, the value at the same location (that is, column 4, row 1) is G; therefore, in the coded message, G stands for S.
The writer goes through the same process for E. In the constant grid, E appears at column 1 row 5. In the message grid, the value at column 1 row 5 is 2.
The writer repeats the foregoing steps for each remaining letter. This is the coded result:
G2HFR02
Because it may be undesirable to use the same character equivalences for every message, the key-word grid can be used to change character equivalences for any particular message. For example, if Signet is chosen from the key-word grid as the key word for a particular message, the writer of the message would follow the steps described above to create another message grid. Then, using the new message grid, SEYMORE is rendered thus in the resulting cipher:
1L2ZBTL
Space and punctuation are not included in the foregoing configurations of the cipher.
While this approach to cipher achieves encoding, the very appearance of coded material in a document announces the presence of such a message. And that announcement invites de-ciphering; meaning, of course, that all secrecy depends upon the fastness of the code. It were better to have a symbology for presenting the ciphered message; a symbology that does not announce the existence of a message. In other words, we sought a way of encoding not only the substance of a message, but the characters constituting the cipher. Ideally, such a symbology would be perceived as a visual, instead of a linguistic, element in the communication. Ideally, it would not be perceived as part of a communication at all.
The following divulges an early attempt at such a symbology. This is the point in this explanation of the Six-Square Cipher that another level of complexity is introduced. Intended use of the cipher must determine whether the added complexity is necessary.
As I worked on designing the following glyphs, for use with the Six-Square Cipher, they came to remind me of the signal banners used by skippers on the high seas. Accordingly, I called them pennants; nevertheless, I did not design these glyphs with any reference to such banners, but simply began the task of design with the objective of creating a set of simple graphics that would, in their variation provide enough distinct characters to accommodate at least 36 characters. I wanted visual objects that could be included in a decorative border, or some such usage apart from the written text of a message.
My design effort eventually resulted in 43 glyphs. Since there are only 36 characters in the stream, the set of 43 provided for a substantial number of meaningless glyphs that could be included in a message without affecting its content. Their inclusion would, of course, pose a considerable impediment to anyone attempting to decipher the pattern. Meaningless elements delay and can even frustrate the task of deciphering. It is imperative, however, that the use of meaningless glyphs fit a pattern of repetition unconnected with the repetition pattern in the significant glyphs. They must be used in a pattern of their own, and that pattern must not be connected to the pattern of the "real" glyphs.
In the accompanying glyph chart, the sequence of the glyphs is not significant. The glyphs and the key words are simply assigned one to another. Unassigned glyphs become the dummy glyphs that can be incorporated into the coded message for the purpose of obfuscation.
Once the key words have been assigned to the glyphs, the key word for a particular message (Lilium, for example) determines which of the glyphs represents the letter A. Once the glyph for A is identified, the remaining values in the stream are determined sequentially. This use of the key-word list means that a single key word serves for a coded message whether its cipher is simple (that is, uses only stream values for its cipher) or complex (uses a visual corollary for the representation of its cipher). These assignments are reflected in the following additions to the message grid for Lilium (not the constant grid).
Given the value assignments in the message grid for Lilium, this is how SEYMORE would be rendered in pennants with Lilum as the key word for the cipher.
The following facsimile is the second worksheet found in the folio mentioned, above. Seymore's notes prefigure his refinement of the Six Square Cipher into what became known as The Diamond Pavillion, a methodology of encryption that eventually transformed coded transcriptions into an art form.
The folio in which the memorandum was found also contained two sheets of paper, later identified as some of Seymore's worksheets prepared in creating and refining the cipher. Those worksheets are presented here with scant annotation. One of the sheets presents an early version of what Seymore referred to as pennants, mentioned in Seymore's memorandum. The other sheet contains ideas about enhancing the cipher through further work with the pennants.
 |
| Facsimile of Worksheet 1 |
Seymore's reminiscences appear to remark a thread of interest in the subject from his early youth, for he mentions his childhood fascination with "secret alphabets," and his preoccupation with the very idea of coded messages carried by the couriers that were so prominent a feature of his youth (owing to Bevel Wainscott's sprawling enterprise). Most importantly, however, Seymore speaks at length of his experience with his maternal grandfather, the great Foliaceous Gatherum.
When Bevel and his small household relocated to Lanham in 1757, Seymore, along with the rest of the family, was caught up in the devastating consequences of Bevel's illness. During that time, Foliaceous reached out to his grandson, undoubtedly perceiving much of kindred interest and ability in the youth. In order to throw a lifeline to Seymore during those troubled times, Foliaceous not only reached out to the youth, but did so in terms of Seymore's own interests and imagination. The bond between the two was fixed for life, and set Seymore's feet upon the high road he traveled throughout his life. Grandfather and grandson exchanged encrypted letters even though they were essentially living in the same household. And one of the facets of the exchange was Seymore's exposure to the languages by which the lytfolc had labored for centuries to preserve their history; languages that in times of peril had involved codes and ciphers, tokens and clues of amazing invention.
A Brief Description Of The Six Square Cipher
Created By Seymore Wainscott
The following sequence of 36 characters is referred to hereafter as the stream: ABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890
| Facsimile of Stream |
 |
| Facsimile of Grid |
A G M S Y 5
B H N T Z 6
C I O U 1 7
D J P V 2 8
E K Q W 3 9
F L R X 4 0
The constant grid looks like this:
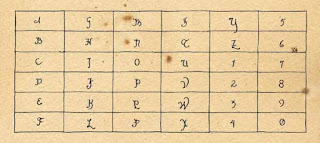 |
| Facsimile of Constant Grid |
Hominy
Mulberry
Rosette
Transom
Newel
Tracery
Finial
Burrow
Signet
Rune
Pargetry
Ovolo
Boss
Anthem
Medallion
Penton
Sorrel
Lupine
Thwaite
Folio
Quarto
Corbel
Scotia
Lilium
Calyx
Currant
Quince
Marjoram
Lichen
Tasselin
Teviot
Sable
Gentian
Trillium
Lancet
Acorn
Draw another grid six cells high and six cells wide.
Assign each name in the key-word list to a cell in the empty grid. The order in which the names are assigned is of no moment. In the following grid, the names were assigned (north-to-south and west-to-east) in the order in which they appear in the key word list. This is referred to as the key-word grid.
Hominy Finial Boss Thwaite Calyx Teviot
Mulberry Burrow Anthem Folio Currant Sable
Rosette Signet Medallion Quarto Quince Gentian
Transom Rune Penton Corbel Marjoram Trillium
Newel Pargetry Sorrel Scotia Lichen Lancet
Tracery Ovolo Lupine Lilium Tasselin Acorn
The key-word grid looks like this:
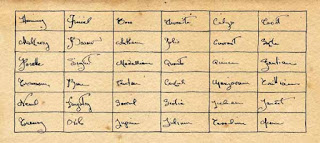 |
| Facsimile of Key-word Grid |
Draw another grid six cells high and six cells wide.
Select the name of a cell, in the key-word grid, at which to begin assigning stream values. For example, if Lilium is the keyword chosen for this purpose (that is, for creating a particular coded communication), the values in the stream are assigned beginning with the cell named Lilium in the key-word grid. The first four assignments of stream values look like this in the grid just drawn,
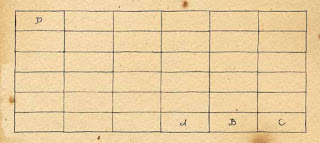 |
| Facsimile of Lilium Grid |
D E F G H I
J K L M N O
P Q R S T U
V W X Y Z 1
2 3 4 5 6 7
8 9 0 A B C
Given the stream-value cell assignments in the constant grid, the following list presents the letter equivalents for a coded message whose key word is Lilium.
For example, to write SEYMORE in cipher, according to the foregoing message grid, the person writing the message would first look for the location of S in the constant grid. In the constant grid, S is located in the 4th column and on the 1st row. Now, referring back to the message grid, the value at the same location (that is, column 4, row 1) is G; therefore, in the coded message, G stands for S.
The writer goes through the same process for E. In the constant grid, E appears at column 1 row 5. In the message grid, the value at column 1 row 5 is 2.
The writer repeats the foregoing steps for each remaining letter. This is the coded result:
G2HFR02
Because it may be undesirable to use the same character equivalences for every message, the key-word grid can be used to change character equivalences for any particular message. For example, if Signet is chosen from the key-word grid as the key word for a particular message, the writer of the message would follow the steps described above to create another message grid. Then, using the new message grid, SEYMORE is rendered thus in the resulting cipher:
1L2ZBTL
Space and punctuation are not included in the foregoing configurations of the cipher.
While this approach to cipher achieves encoding, the very appearance of coded material in a document announces the presence of such a message. And that announcement invites de-ciphering; meaning, of course, that all secrecy depends upon the fastness of the code. It were better to have a symbology for presenting the ciphered message; a symbology that does not announce the existence of a message. In other words, we sought a way of encoding not only the substance of a message, but the characters constituting the cipher. Ideally, such a symbology would be perceived as a visual, instead of a linguistic, element in the communication. Ideally, it would not be perceived as part of a communication at all.
The following divulges an early attempt at such a symbology. This is the point in this explanation of the Six-Square Cipher that another level of complexity is introduced. Intended use of the cipher must determine whether the added complexity is necessary.
As I worked on designing the following glyphs, for use with the Six-Square Cipher, they came to remind me of the signal banners used by skippers on the high seas. Accordingly, I called them pennants; nevertheless, I did not design these glyphs with any reference to such banners, but simply began the task of design with the objective of creating a set of simple graphics that would, in their variation provide enough distinct characters to accommodate at least 36 characters. I wanted visual objects that could be included in a decorative border, or some such usage apart from the written text of a message.
My design effort eventually resulted in 43 glyphs. Since there are only 36 characters in the stream, the set of 43 provided for a substantial number of meaningless glyphs that could be included in a message without affecting its content. Their inclusion would, of course, pose a considerable impediment to anyone attempting to decipher the pattern. Meaningless elements delay and can even frustrate the task of deciphering. It is imperative, however, that the use of meaningless glyphs fit a pattern of repetition unconnected with the repetition pattern in the significant glyphs. They must be used in a pattern of their own, and that pattern must not be connected to the pattern of the "real" glyphs.
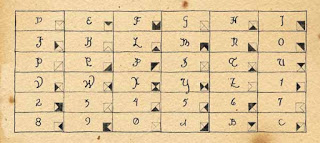
In the accompanying glyph chart, the sequence of the glyphs is not significant. The glyphs and the key words are simply assigned one to another. Unassigned glyphs become the dummy glyphs that can be incorporated into the coded message for the purpose of obfuscation.
 |
| Facsimile of Glyphs |
 |
| Facsimile of Lilium Grid with Glyphs |
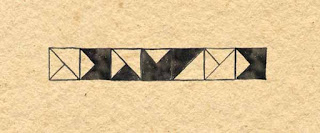 |
| Facsimile of Lilium Glyphs for Seymore |
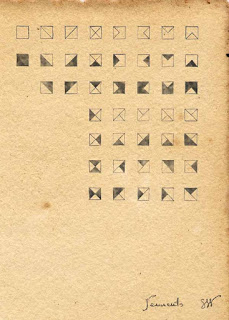 |
| Facsimile of Worksheet 2 |
Tags: 2013
Browse articles by year: 2025 . 2024 . 2023 . 2022 . 2021 . 2020 . 2019 . 2018 . 2017 . 2016 . 2015 . 2014 . 2013 . 2012 . 2011 . 2010 . 2009 . 2008 . 2007 . 2006 . 2005 . 2004 . 2003 . 2002 . 2001 . 2000 . 1999 . 1998 . 1997 . 1996
Browse articles by topic: Art lessons . BenHaven Archives . Blank art diaries . Fine art photography . Framing . Illustration . Inspiration and creativity . Isles of Rune . Limited Editions Collection . My Fathers Captivity . News . Novellas . Oil paintings and prints . Operations announcements . Orders and shipping . Overview . Portfolios . The Papers of Seymore Wainscott . Project commentaries . Recipes by Nancy Young . Recommended reading . Recommended viewing . Temple artworks . The Storybook Home Journal . Tips and techniques . Tools supplies and operations
Browse articles by topic: Art lessons . BenHaven Archives . Blank art diaries . Fine art photography . Framing . Illustration . Inspiration and creativity . Isles of Rune . Limited Editions Collection . My Fathers Captivity . News . Novellas . Oil paintings and prints . Operations announcements . Orders and shipping . Overview . Portfolios . The Papers of Seymore Wainscott . Project commentaries . Recipes by Nancy Young . Recommended reading . Recommended viewing . Temple artworks . The Storybook Home Journal . Tips and techniques . Tools supplies and operations